What does a network audit look like?
Summary
A network audit is a comprehensive review of the cybersecurity policies and infrastructure used to protect a network. It involves identifying threats, conducting assessments, and preparing audit reports for management and stakeholders to review.
1. What is included in a network audit?
A network audit includes a review of cybersecurity policies, identification of threats, and the creation of formal audit reports.
2. How do I prepare for a network audit?
To prepare for a network audit, you need to define the scope of the audit, determine potential threats, review and edit internal policies, evaluate password strategies, ensure data safety, inspect servers, and examine training logs.
3. What should a network security audit include a review of?
A network security audit typically includes a review of all network infrastructure and systems accessible from the internet, as well as the security mechanisms implemented to protect them.
4. What does an audit checklist look like?
An audit checklist is a document or tool used to facilitate an audit program. It contains information such as the scope of the audit, evidence collection, audit tests and methods, analysis of results, and conclusions, as well as follow-up actions like corrective and preventive measures.
5. What are the 5 contents of an audit report?
The basic contents of an audit report include the title, addressee details, opening paragraph, scope paragraph, opinion paragraph, signature, place of signature, and any other relevant information.
6. What are the 5 parts of an audit?
The five parts of an audit are audit objectives, audit procedures and scope, findings and conclusions, recommendations (if applicable), and management’s response.
7. How is auditing done in a network?
A network audit involves collecting data, identifying threats and weaknesses, and compiling a formal audit report to be sent to network administrators and relevant parties.
8. How do you pass an audit?
To pass an audit, you can start with an internal self-assessment, run access checks, keep thorough records, track regulations, and implement training for everyone associated with your company.
9. What is the best tool for network audit?
Some popular and effective tools for network audits include Intruder, ManageEngine Vulnerability Manager Plus, Atera, ManageEngine Log360, Netwrix Auditor, Nessus, and Nmap.
10. What is a security audit checklist?
A security audit checklist is a list of security measures and practices that must be implemented to protect an organization’s information systems and data from various threats.
11. What are the 5 C’s of an audit finding?
The 5 C’s of an audit finding are criteria, condition, cause, consequence, and corrective action. These elements help in evaluating and addressing audit findings effectively.
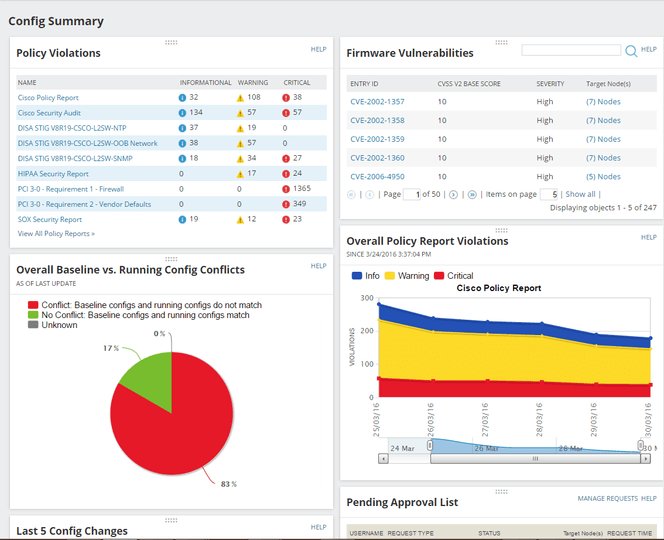
What is included in a network audit
A network audit involves a review of the cybersecurity policies used to protect the network. After identifying the threats, a formal audit report is made, which is then sent to the management and other stakeholders for review.
Cached
How do I prepare for a network audit
Network Security Audit ChecklistDefine the Scope of the Audit.Determine Threats.Review and Edit Internal Policies.Reevaluate Your Password Strategies.Ensure the Safety of Sensitive Data.Inspect the Servers.Check the Procedure Management System.Examine Training Logs.
Cached
What should a network security audit include review of
A network security audit usually consists of a review of all network infrastructure and systems accessible from the internet. It also involves a review of the security mechanisms used to protect the network infrastructure, including the network devices.
Cached
What does an audit checklist look like
An audit checklist may be a document or tool that to facilitate an audit programme which contains documented information such as the scope of the audit, evidence collection, audit tests and methods, analysis of the results as well as the conclusion and follow up actions such as corrective and preventive actions.
What are the 5 contents of an audit report
Audit Report Contents are the basic structure of the audit report which needs to be clear, providing sufficient evidence providing the justification about the opinion of the auditors and includes Title of Report, Addressee details, Opening Paragraph, scope Paragraph, Opinion Paragraph, Signature, Place of Signature, …
What are the 5 parts of an audit
(i) Audit objectives; (ii) Audit procedures and scope; (iii) Findings and conclusions; (iv) Recommendations, if applicable; and (v) Management's response.
How is auditing done in a network
A network audit entails collecting data, identifying threats and areas of weakness, and compiling a formal audit report. This report is then sent on to network administrators and other relevant parties.
How do you pass an audit
How to Pass An AuditStart with an internal self-assessment.Run an access check.Keep thorough records.Track the latest regulations.Implement training for everyone associated with your company.
What is the best tool for network audit
Intruder (FREE TRIAL)ManageEngine Vulnerability Manager Plus (FREE TRIAL)Atera (FREE TRIAL)ManageEngine Log360 (FREE TRIAL)N-able N-sight.Netwrix Auditor.Nessus.Nmap. Nmap is an open-source port scanner and network security scanner.
What is security audit checklist
An information security audit checklist is a list of security measures that must be taken to protect an organization's information systems and data from various threats. This checklist aims to promote best practices of information security and guide how information should be managed, stored, and secured.
What are the 5 C’s of an audit finding
What Are the 5 C's of Internal Audit Internal audit reports often outline the criteria, condition, cause, consequence, and corrective action.
What are the 4 C’s of audit findings
Internal audit reports often outline the criteria, condition, cause, consequence, and corrective action.
What are the 4 C’s of audit report writing
Criteria, Condition, Cause, Consequence, and Corrective Action Plans/ Recommendations.
What are the 4 C’s of internal audit
culture, competitiveness, compliance and cybersecurity
As for directors, there are four features to consider when evaluating the sufficiency of any risk-based audit plan: culture, competitiveness, compliance and cybersecurity – let's call them the Four C's, for short.
What are the three steps in auditing
The process employed by the Office of Internal Audit in performing audits follows three general phases comprising planning, fieldwork, and reporting.
What not to say during an audit
10 Things Not to Say in an Audit ReportDon't say, “Management should consider . . .”Don't use weasel words.Use intensifiers sparingly.The problem is rarely universal.Avoid the blame game.Don't say “management failed.”7. “Avoid uunnecessary technical jargon.
Is audit hard to pass
AUD has the second lowest pass rate (the lowest is FAR), likely because many CPA candidates do not have a background in auditing. If you are one of those candidates who is not overly familiar with auditing, you will likely want to take FAR first to take advantage of any overlapping financial accounting content.
What are the three primary tools that are used in the IM audit
Three main types of auditing tools are there. They are, External audits, Internal audits, and Internal Revenue Service audits.
How do I review network security
How to Conduct a Network Security AssessmentTake inventory of your resources.Determine information value.Assess the vulnerability of your IT infrastructure.Test your defenses.Document results in a network security assessment report.Implement security controls to improve cybersecurity.
Which questions are assessed in a security audit
Top 5 IT Security Audit QuestionsDo you have a documented security policyAre access privileges in your organisation granted adequatelyWhat methods do you use to protect your dataDo you have a disaster recovery planAre your employees familiar with existing security procedures and policies
What is the 5 7 rule auditing
The 5/7 rule provides that an individual may not play a significant role in the audit of a particular audited body for more than 5 out of 7 successive financial years.
What are the 4 categories of audit findings
They include:Clean Report or Unqualified Opinion.Qualified Report or Qualified Opinion.Disclaimer Report or Disclaimer of Opinion.Adverse Audit Report or Adverse Opinion.
What are the 5 elements of audit finding
There are five elements of a finding:Condition: What is the problem/issue What is happeningCause: Why did the condition happenCriteria: How do we, as auditors, know this is a problem What should beEffect: Why does this condition matter What is the impactRecommendation: How do we solve the condition
What are the 7 principles of internal audit
The principles of independence, objectivity, competence, confidentiality, professionalism, due professional care, and continuous improvement are essential for the internal audit function to fulfill its role as a trusted advisor to the organization.
What are the 5 components of internal audit
Determining whether a particular internal control system is effective is a judgement resulting from an assessment of whether the five components – Control Environment, Risk Assessment, Control Activities, Information and Communication, and Monitoring – are present and functioning.



0 Comments